In order to safeguard the anonymity of suppliers, a series of essential configurations must be carried out within the system. These steps involve manipulating security roles, data security policies, and role hierarchies to ensure that sensitive information, particularly Personally Identifiable Information (PII), remains protected. The following guide outlines the specific actions needed to obscure supplier details effectively.
- To obscure the identity of suppliers, you need to perform the following steps:
- Go to Tools – Security Console.
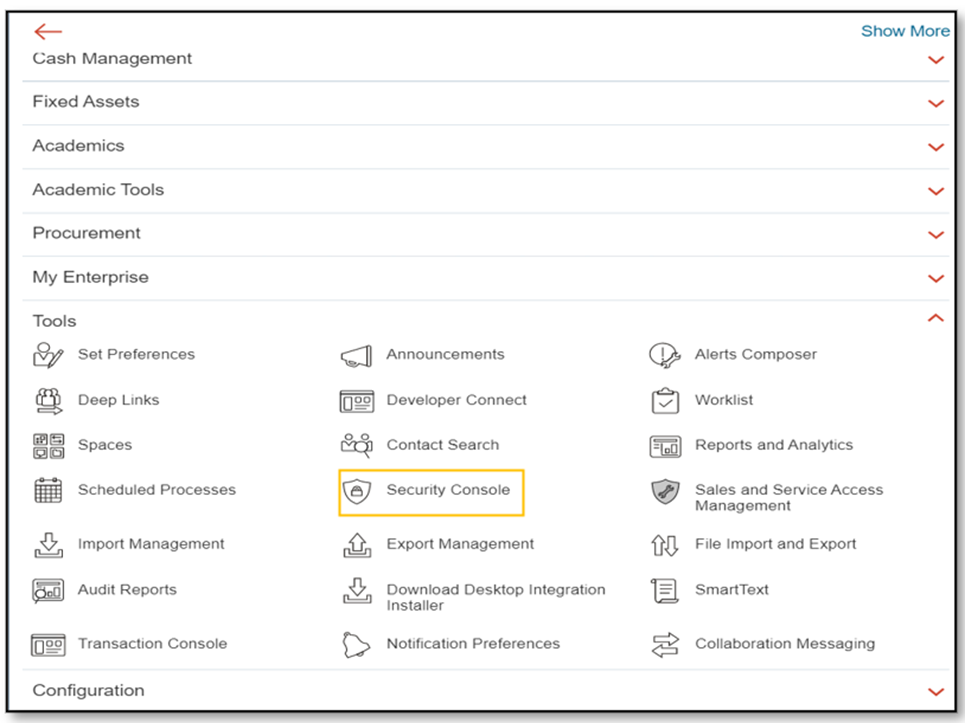
- Enter the Job Role and duplicate that Role.
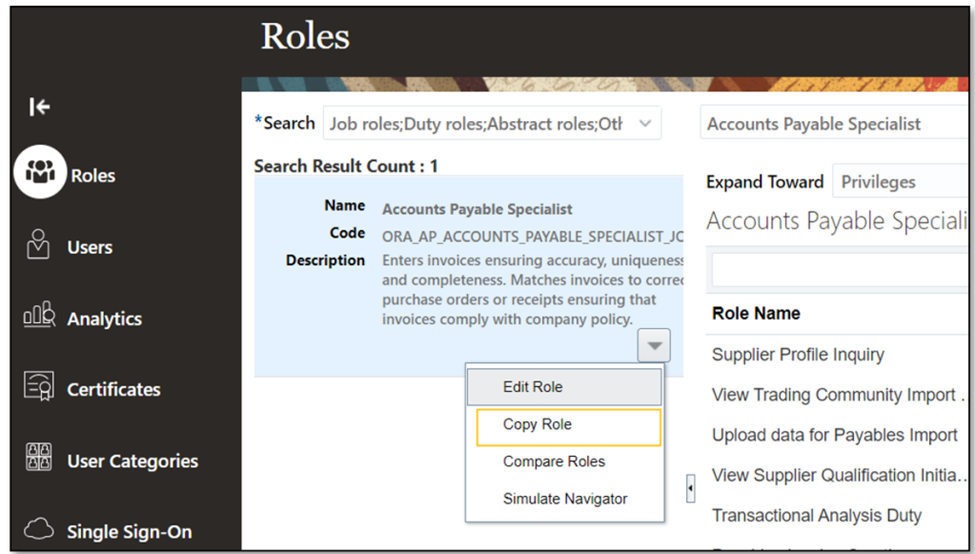
- Duplicate the Account Payables Specialist Job Role and choose “Copy top role” instead of ‘Copy top role and inherited roles.’
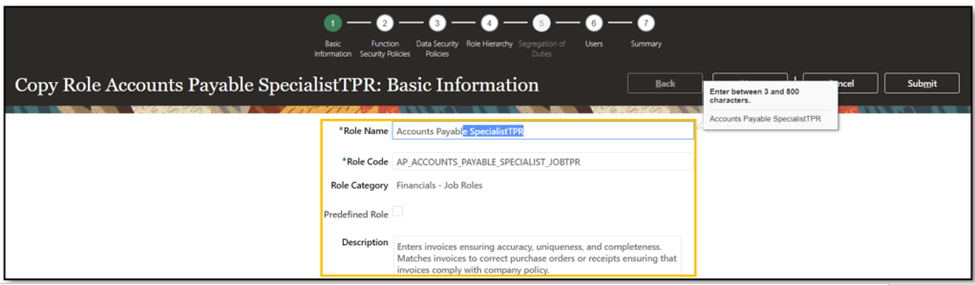
- Click on Next.
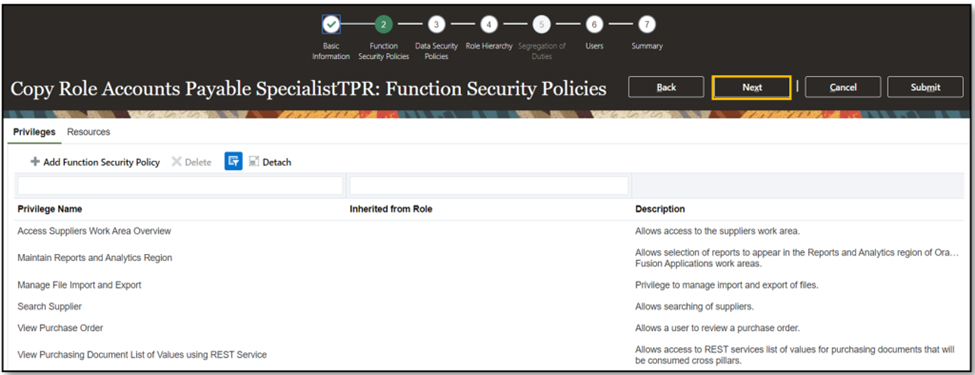
- In Data Security Policies, set an end date for Data Security Policies associated with PII access (two are highlighted, but select all that grant access to PII). Search for the privilege “PII.”
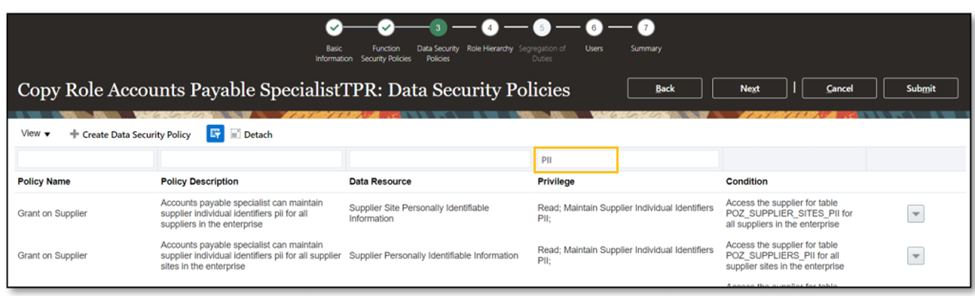
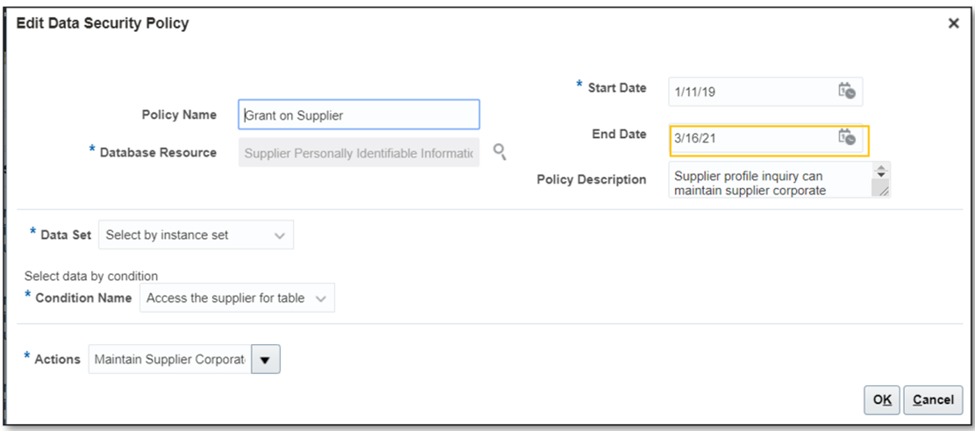
- Populate the end date with yesterday’s date to deactivate the assured Data Security Policies (DSP).

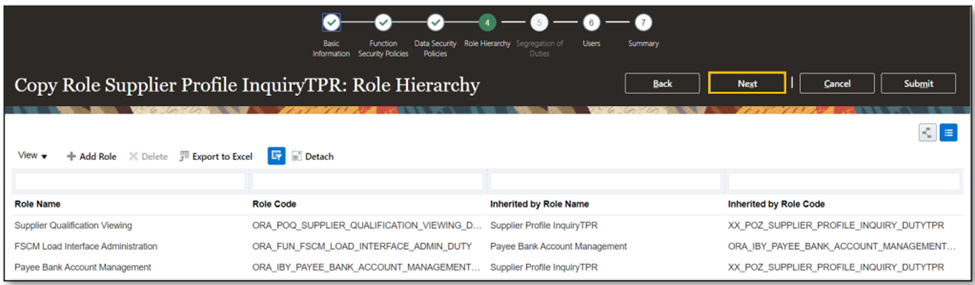
- In the Role Hierarchy, delete the Party Taxpayer Identifier (PII) role. Click ‘Next’ and move to Summary and Report.
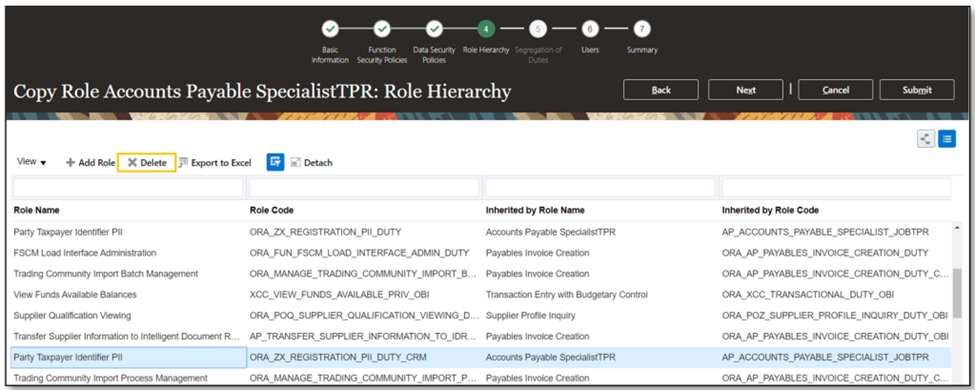
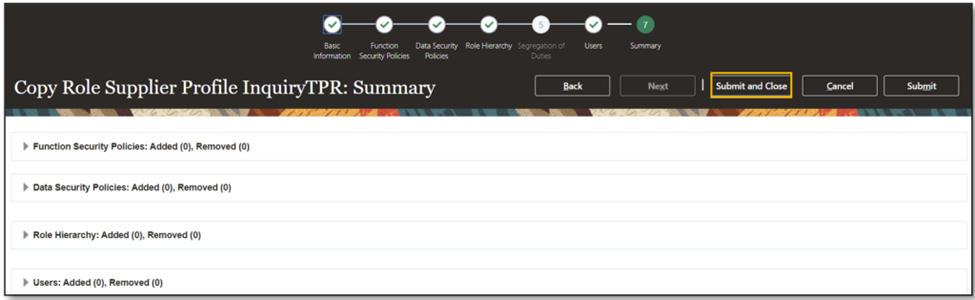
- Continue through the ‘Copy Role’ user interface until you save and close on the Summary and Impact Report Node.
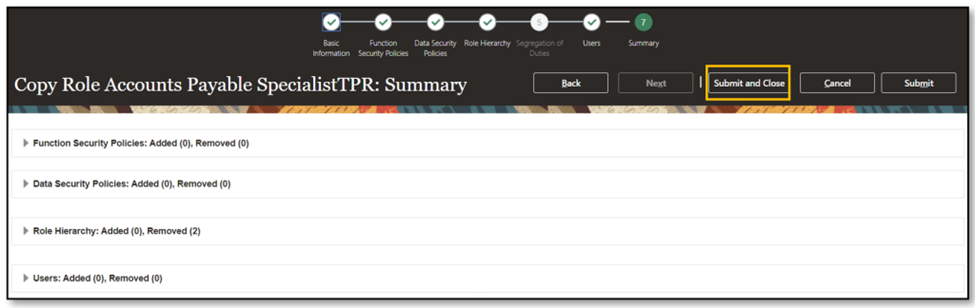
- Submit and close.
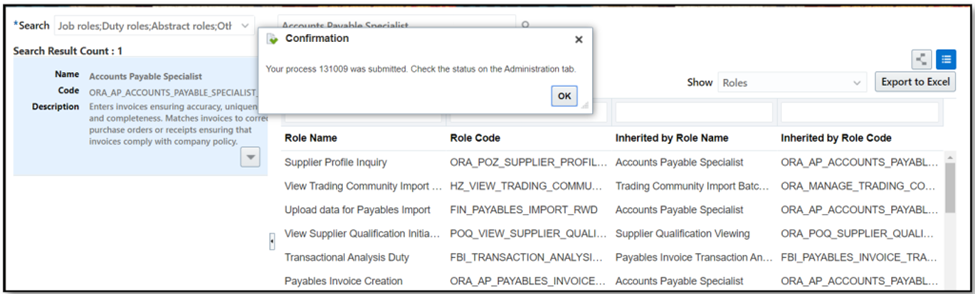
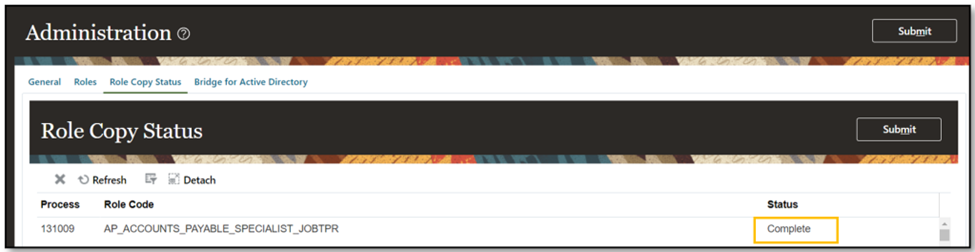
- Verify that the ‘Role Copy Status’ changes to ‘Complete.’
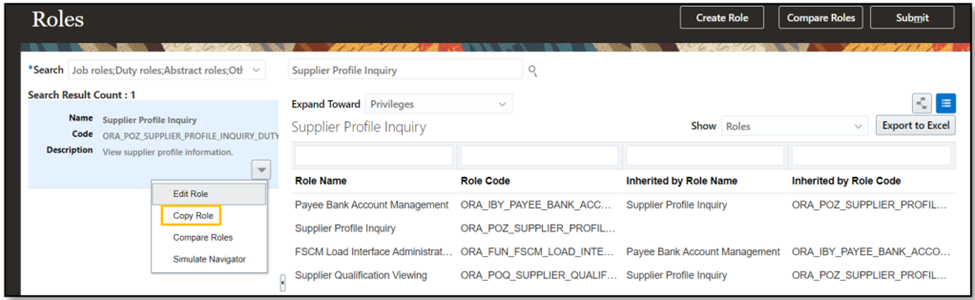
- Duplicate the Supplier Profile Inquiry Duty Role.
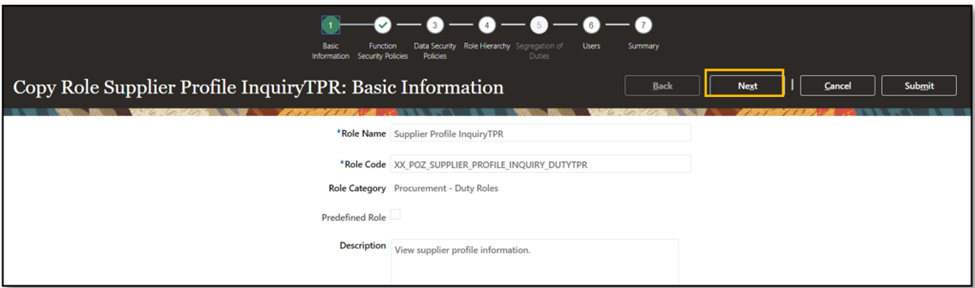
- Click ‘Next.’
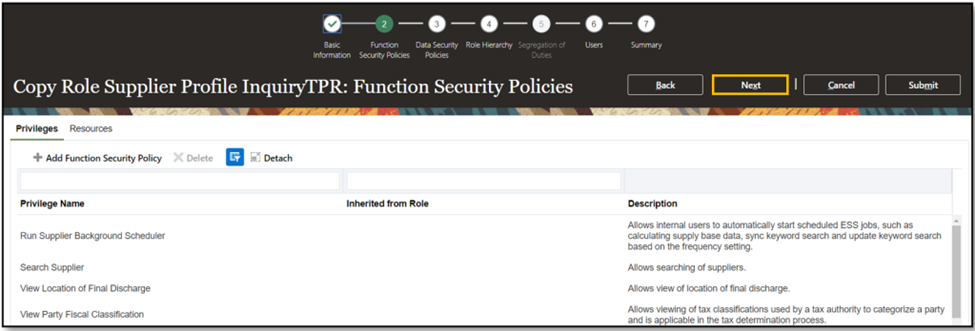
- Click ‘Next.’
- Search for policies containing “Ident” and set an end date for all of them.
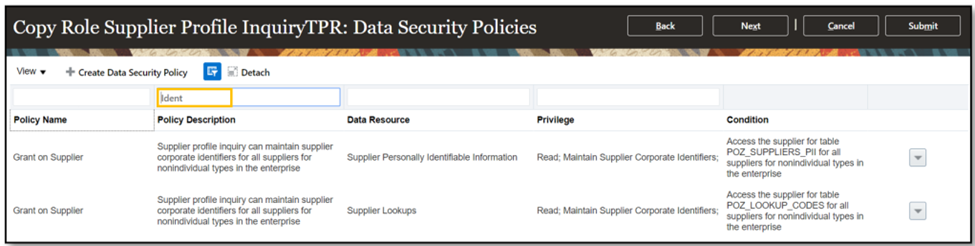
- End date the policies with yesterday’s date.
- Click ‘Next.’
- Submit and close.
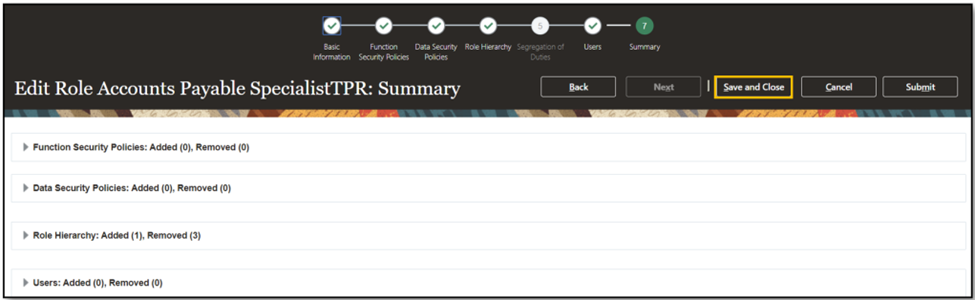
- Edit the “Account Payable SpecialistTPR” Role.
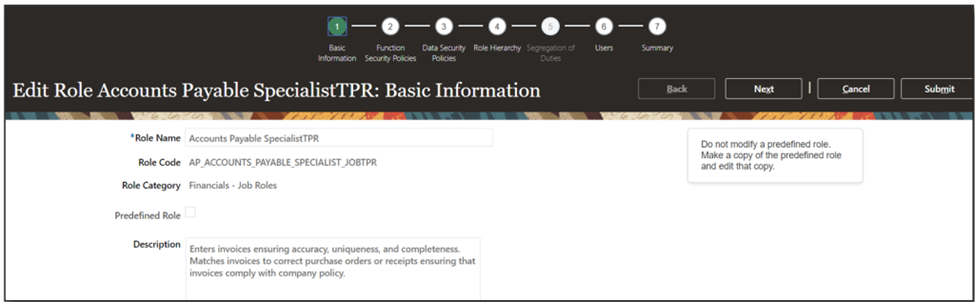
- Remove all instances of the “Supplier Profile Inquiry” role from the role hierarchy.
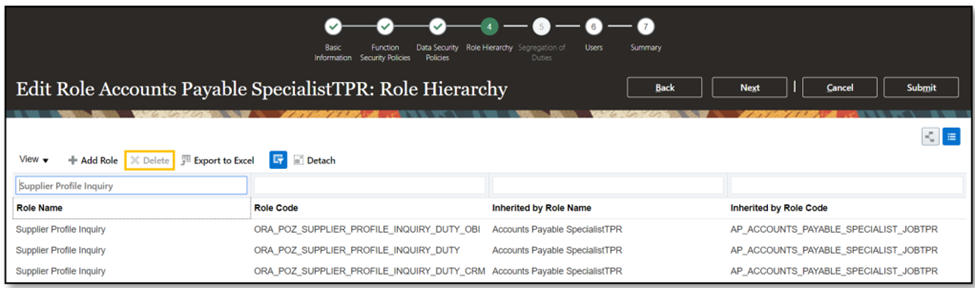
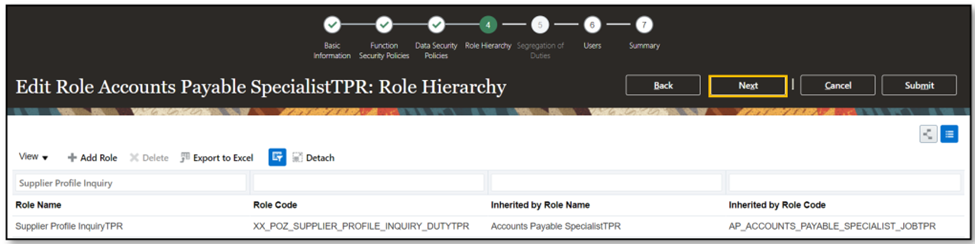
- Include the “Supplier Profile Inquiry TPR” role which has been created in the hierarchy.
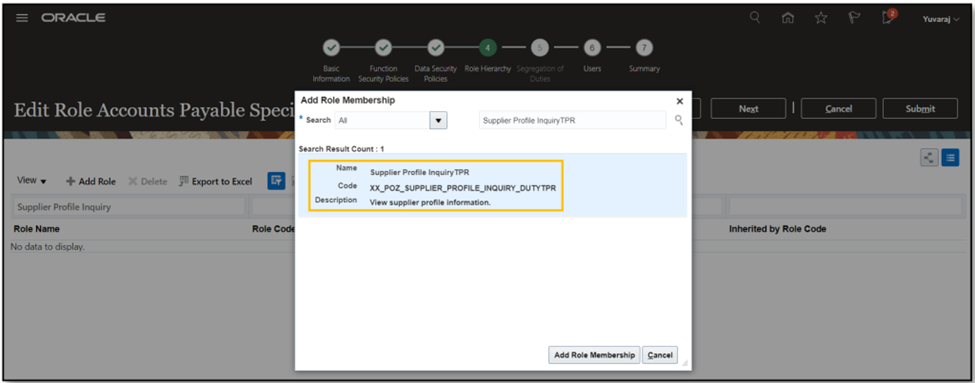
- Click on Next.
- Click on “Save and Close.”
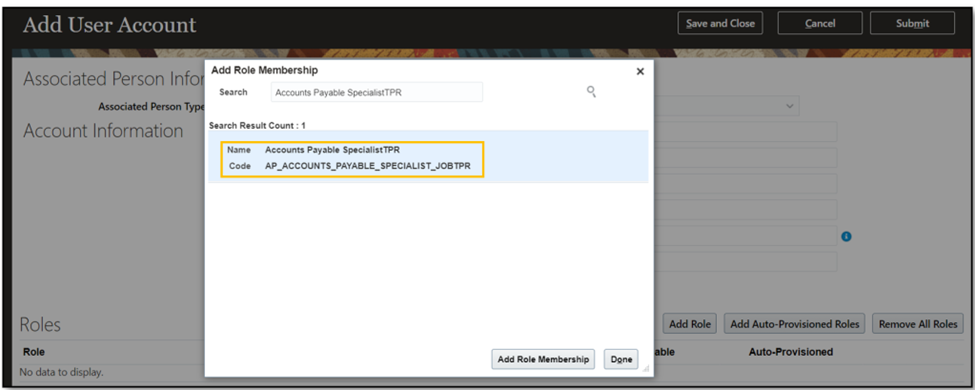
- Assign the ‘Account Payable Specialist TPR’ job role to a new user.
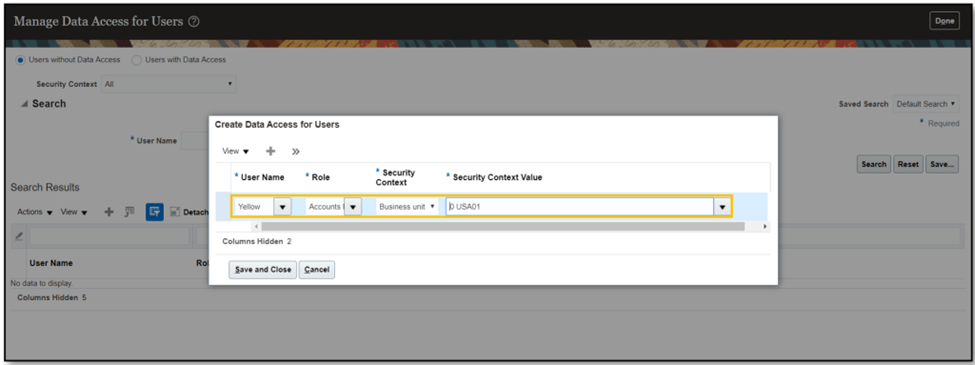
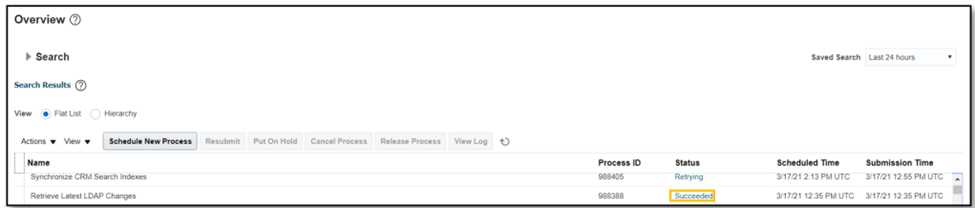
- Provide Business Unit access for the role and run the LDAP synchronization process.
- Navigate to Procurement – Suppliers.
- Query the supplier in the “Manage Suppliers” UI, and the taxpayer ID will be masked with asterisks.
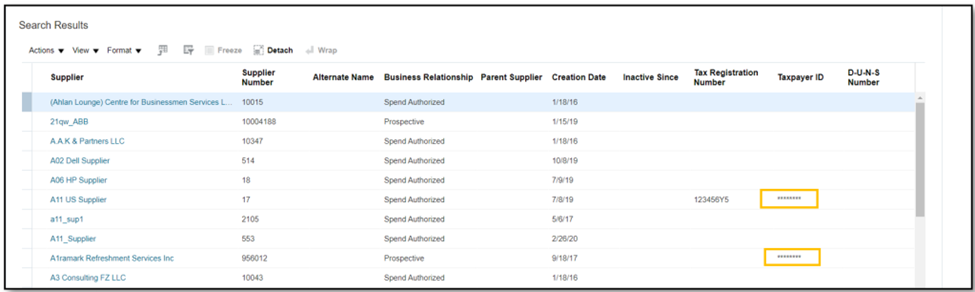
By following these meticulous steps, organizations can ensure the protection of supplier identities and sensitive data within their systems. Properly configured security roles and data policies play a pivotal role in safeguarding the integrity of Personally Identifiable Information. Ultimately, this process enhances data security and privacy, which is of paramount importance in today’s digital landscape.

Leave a Reply