Access Certification is a critical component of ensuring data security and regulatory compliance within organizations. It involves defining roles and responsibilities for various individuals involved in the certification process, such as managers, certifiers, and administrators. This blog outlines the steps required to create an access entitlement and initiate the certification process. This process is integral in maintaining the integrity and security of an organization’s data and resources.
Access Certification Duty Roles
- Access Certification Administrator: The Access Certification Administrator’s role involves defining new certifications and supervising the certification process until its finalization.
- Access Certification Certifier: The Access Certification Certifier is responsible for overseeing the certification of specific combinations of roles and user access, organized into worksheets.
- Access Certification Configuration and Maintenance: This role entails the initial configuration of the application and ongoing support for data security policies.
- Access Certification Owner: The Access Certification Owner is responsible for ensuring the completion of a set of worksheet certifications.
Creating an Entitlement
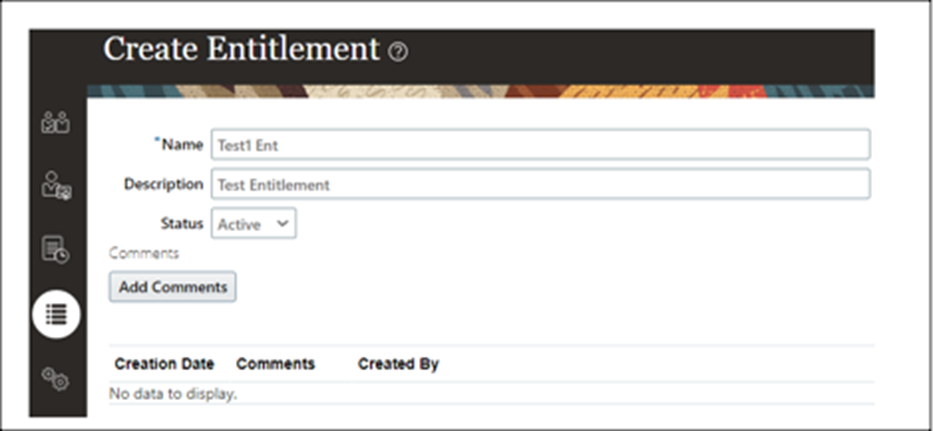
Step 1: Create an Entitlement
- Create a new access entitlement as depicted below
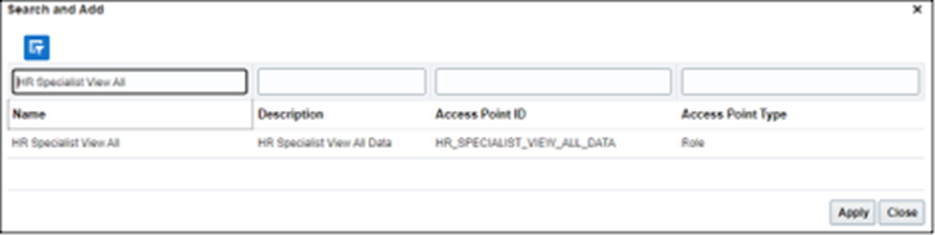
- Add an Access Point.
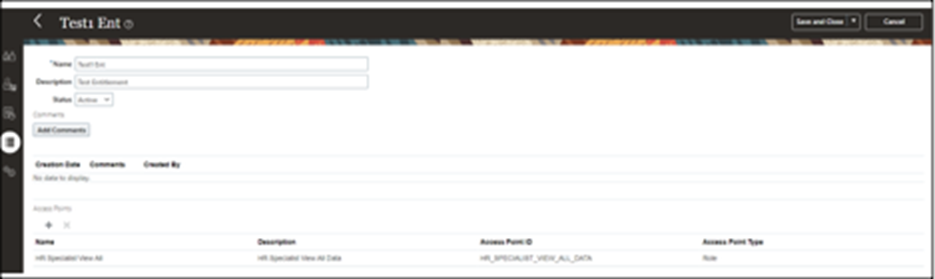
- Click “Save and Close.”
Step 2: Initiate Certification
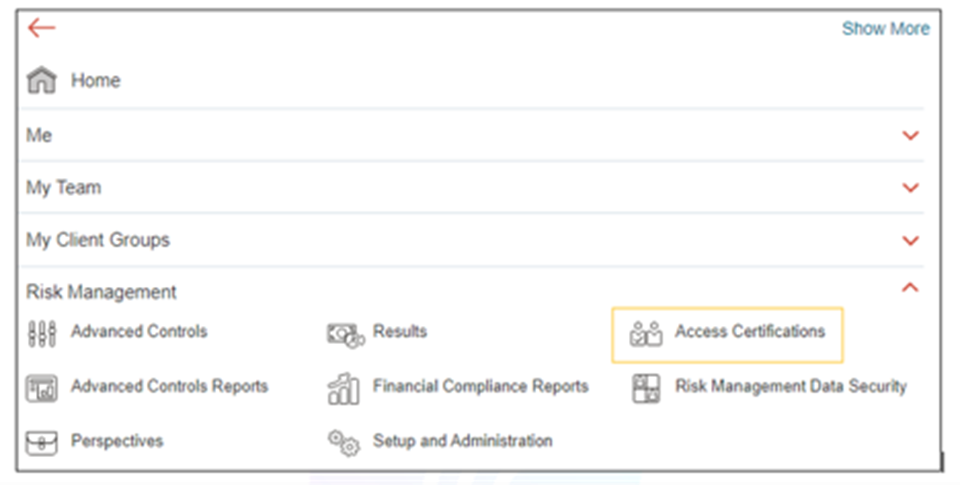
- Navigate to “Risk Management” and select “Access Certification.”
- Click the “Add” icon.
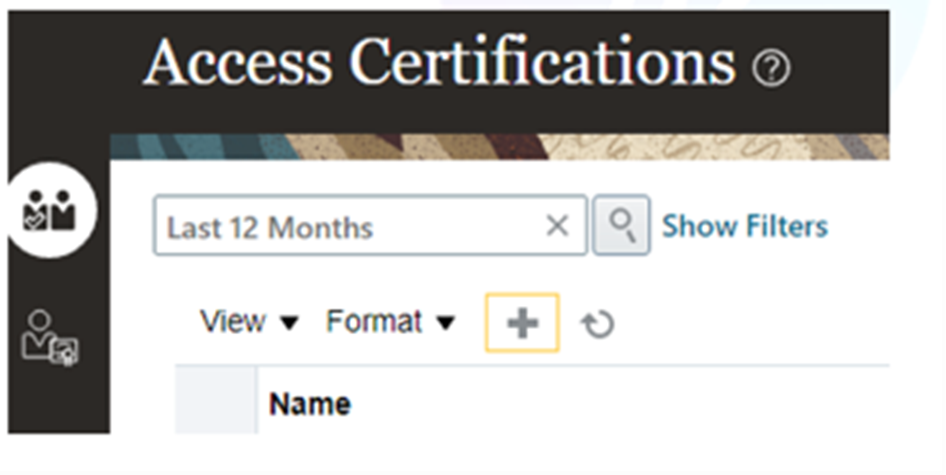
- Enter a description, type, name, and due date.
- Click “Save and Continue.”
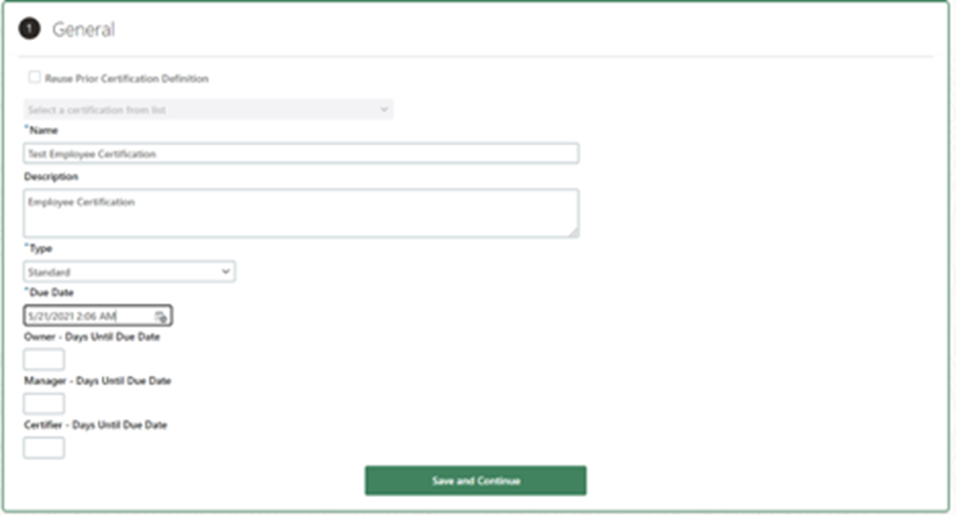
- Click “Save and Continue” again.
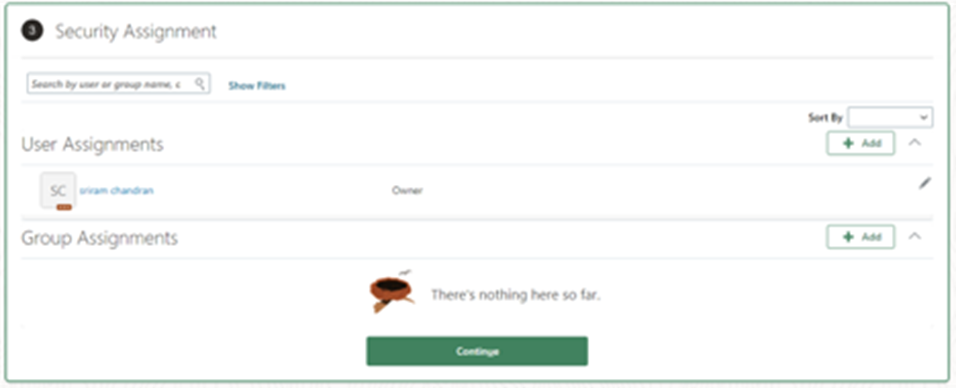
- Click “Add,” select “Authorization,” and click “Save.”
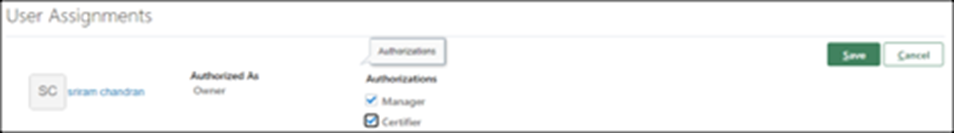
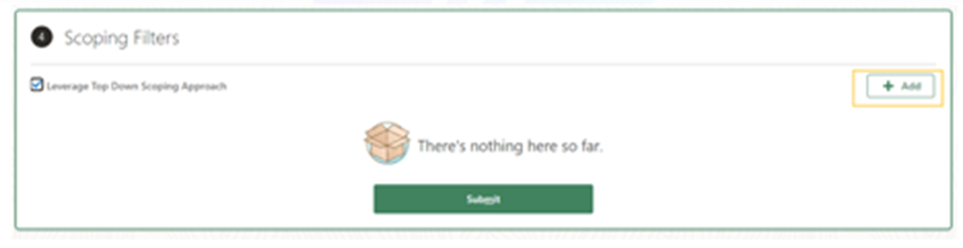
- Add scoping filters.
- Uncheck the ‘Leverage top-down scoping approach’ checkbox.
- Add the specified scoping filter and click ‘Submit.’
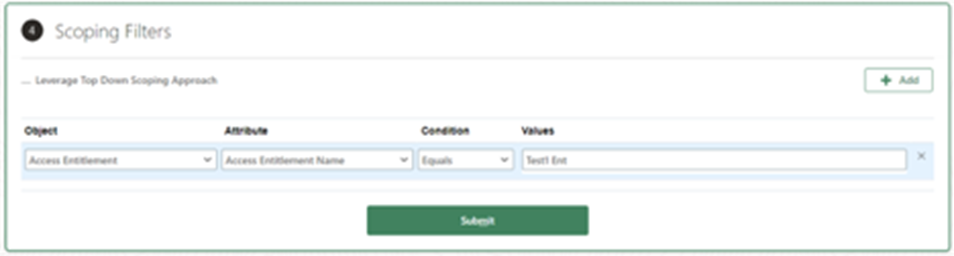
- Click “OK” in the dialog box.
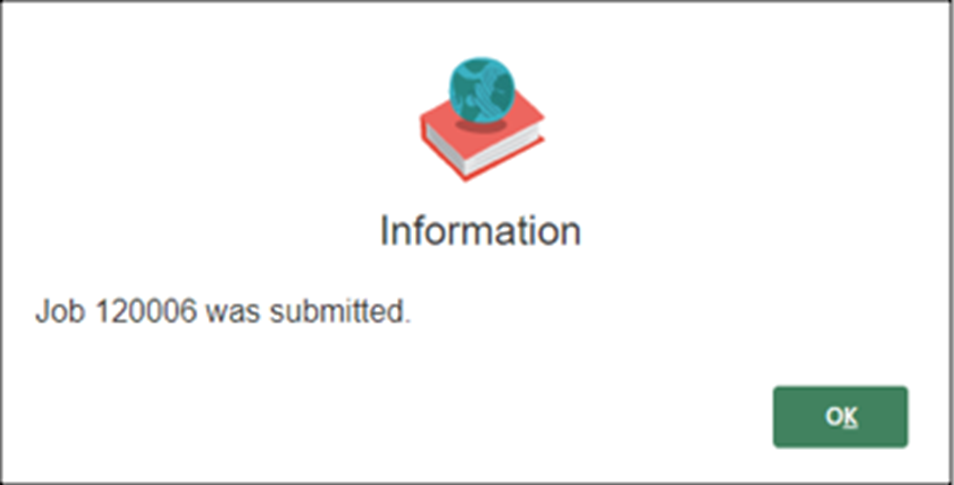
- Monitor the jobs to check if the job is completed.

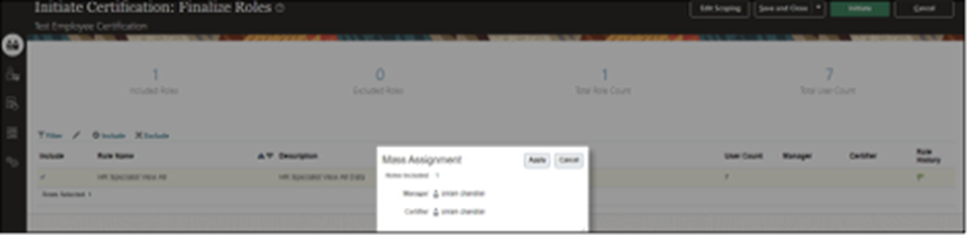
Step 3: Finalize Roles
- Click “Finalize Roles” as depicted.
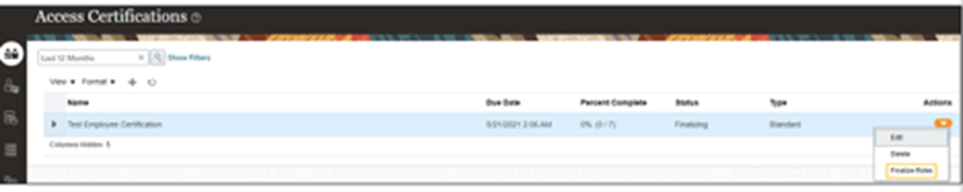
- Assign a manager and certifier for the roles.
- Click “Apply.”
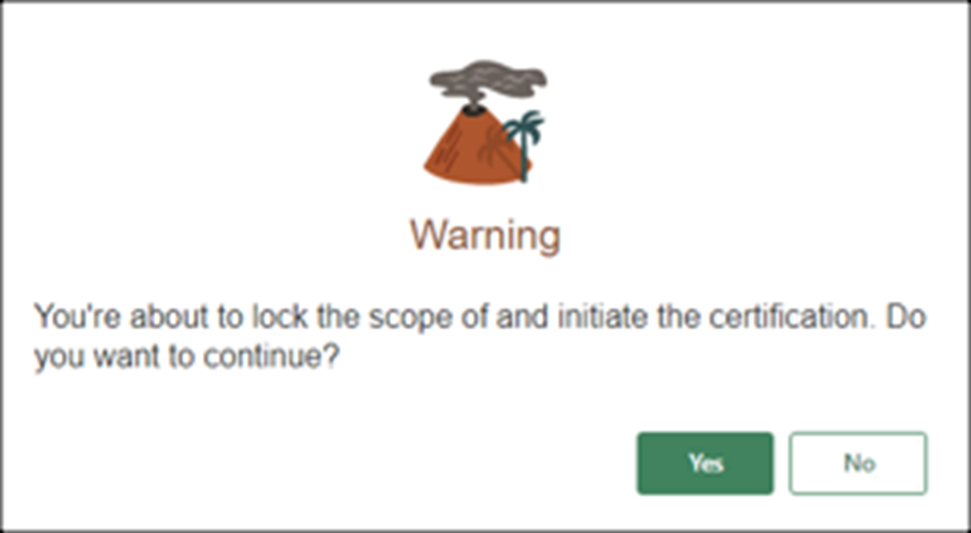
- Click “Initiate.”
- Confirm by clicking “Yes.”
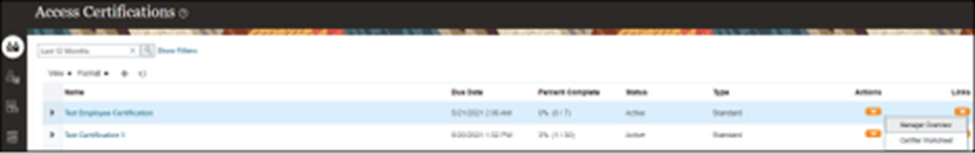
Step 4: Complete Certifier Worksheet
- Click “Certifier Worksheet.”
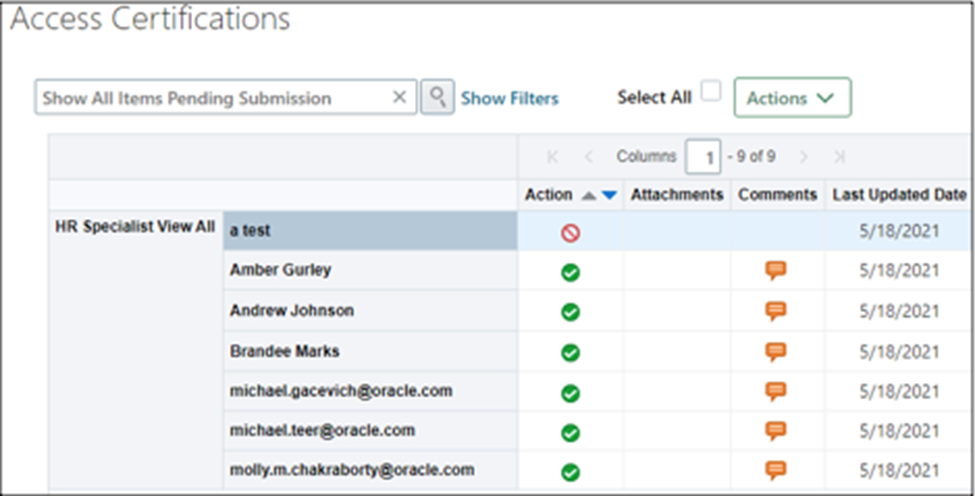
- Select each user to be certified and set the action to ‘approve,’ ‘remove,’ or ‘investigate’ by clicking the appropriate icon.
Step 5: Complete Manager Overview
- Go to “Links” and click “Manager Overview.”
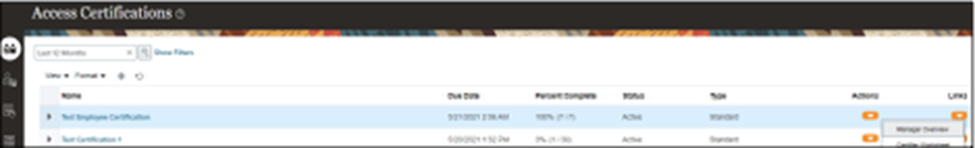
- Review the information and click “Submit.”
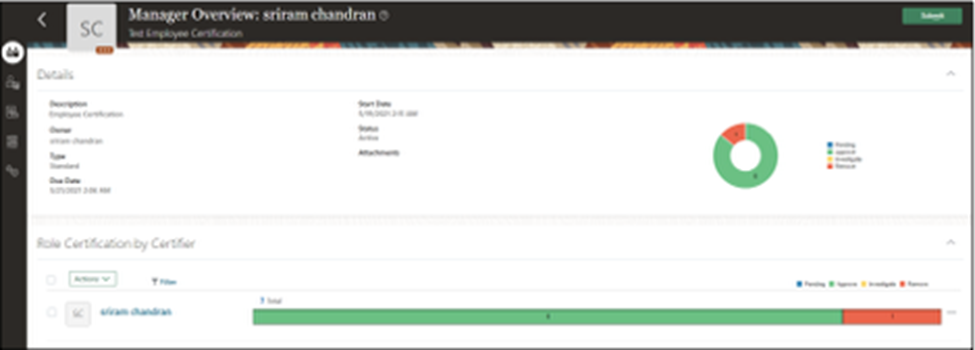
Step 6: Finalize Certification
- Click on the certification name.
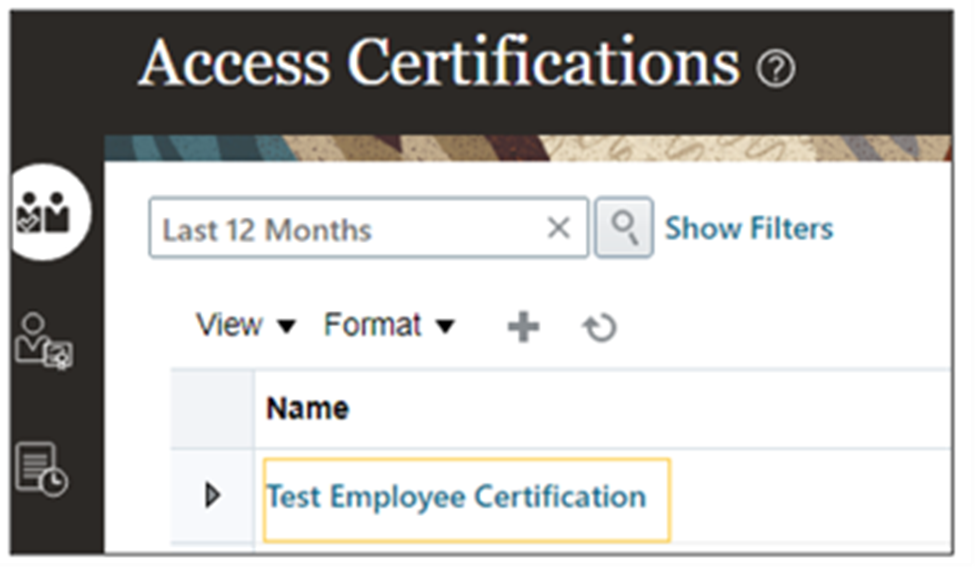
- Select the certifier and click “Finalize Certification.”
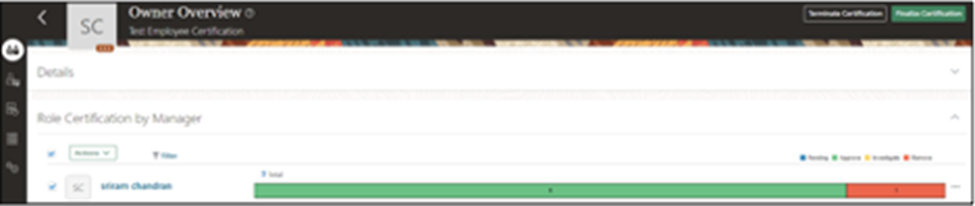
- The status will show as “Closed.”
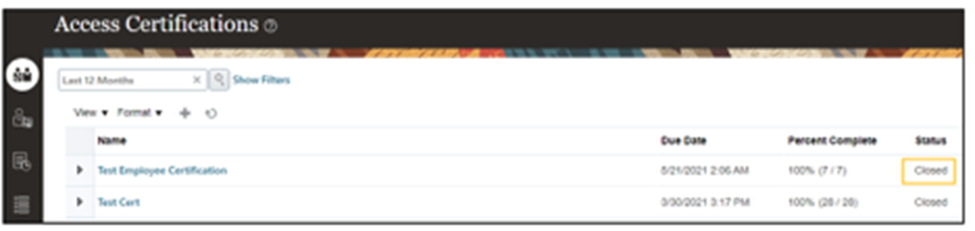
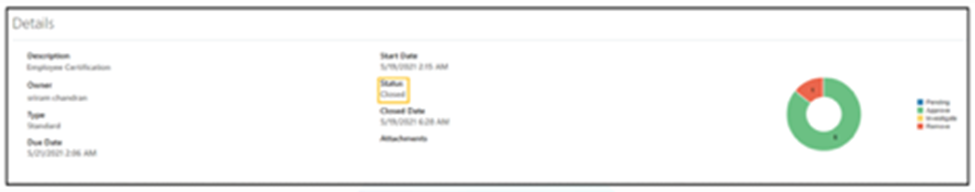
By following the steps outlined for creating an entitlement and finalizing the certification, organizations can strengthen their data security measures and demonstrate their commitment to upholding data integrity and confidentiality.

Leave a Reply